
|
|
About Me | |
|
|
Background | |
|
|
Policy Analysis | |
|
|
Organisations | |
|
|
Cryptography | |
|
|
Technology | |
|
|
Cryptography | |
|
|
Computing | |
|
|
Mathematics | |
|
|
Papers | |
Career History
Education
| 1954-1961 | Southern Grammar School, Portsmouth |
| 1961-1964 | Imperial College, London University (Theoretical Physics Degree) |
| 1970-1973 | Imperial College, London University (Electrical Engineering Ph.D.) |
Career in Defence
| 1964-1967 | Joined Royal Naval Scientific Service at Admiralty Surface Weapons Establishment to work on electronically scanned antennas for ships |
| 1967-1970 | Exchange scientist at the US Naval Electronics Laboratory in San Diego working on theoretical studies of cylindrical electronically scanned antennas |
| 1970-1972 | Returned to UK to continue work on antennas for ships |
| 1972-1980 | Moved to work on the use of computer systems for the automation and support of naval command and control functions |
| 1980-1988 | Moved to Royal Radar Establishment, Malvern to lead defence research on computer applications |
| 1988-1994 | Moved to the Ministry of Defence, London as Director of Strategic Electronic Communications with systems acquisition responsibility for satellite, telecommunications and cryptographic systems |
| 1994-1995 | Became Director of Communications and Information Systems Engineering with responsibility for improving the performance of MOD in computer systems acquisition |
| 1995-1996 | Moved to become Deputy Director of the SHAPE Technical Centre within NATO (The Hague) |
Career Themes
Microwave Antenna Systems for Ships
 I spent the first phase of my career researching electronically
scanned antenna systems for ships. I was involved in mostly theoretical
work on the design of such systems, building computer models of both antennas
and the associated microwave feed systems.
I spent the first phase of my career researching electronically
scanned antenna systems for ships. I was involved in mostly theoretical
work on the design of such systems, building computer models of both antennas
and the associated microwave feed systems.
During this period I spent two years working at the US Naval Electronics Laboratory Center in San Diego building theoretical models of cylindrical antennas and feed systems for mast mounting on ships.
On return to the UK I took up a related theme of designing antennas for ships with very low side-lobes in order to avoid detection. This work formed the basis for my Ph.D. thesis at Imperial College.
Most of this antenna related research involved the use of computer models and during this period I worked on a wide range of early machines including the Ferranti Pegasus, the English Electric KDF9 and the CDC 6600. It was during this work that my interest in computer technology and software design was aroused.
 Computer
Applications - Security and Safety
Computer
Applications - Security and Safety
In 1972 I moved to take up R&D in the defence use of computers in real time command and control applications. Major research issues in this work included design approaches for software and hardware capable of meeting stringent safety and security requirements.
 Although still working for the Navy, I also became heavily
involved in the use of computer systems for the real-time control of aircraft
and missile systems including Rapier, the Ground to Air system then being
designed for the Army.
Although still working for the Navy, I also became heavily
involved in the use of computer systems for the real-time control of aircraft
and missile systems including Rapier, the Ground to Air system then being
designed for the Army.
In 1980 I moved to the Royal Radar Establishment in Malvern to continue the computer applications theme with a major interest in the security and safety issues posed by the automation of defence activities across all three services.
During this period I managed research in the design and development of real-time operating systems, computer based analysis of critical software, security protocol design and implementation, general and special purpose computer language design and the design and development of special microprocessors providing high assurance of correct operation. The work at Malvern on computer security represented the earliest UK government sponsored R&D in this field, predating that at GCHQ by more than a decade.
 Systems
Acquisition
Systems
Acquisition
 In 1988 I moved to the Ministry of Defence in London
to manage the acquisition of strategic communications systems for defence,
including transmission and switching systems, cryptographic equipment and
space based systems.
In 1988 I moved to the Ministry of Defence in London
to manage the acquisition of strategic communications systems for defence,
including transmission and switching systems, cryptographic equipment and
space based systems.
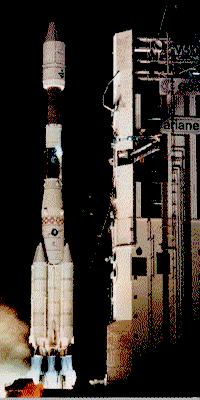
An important part of the work involved the implementation of satellite communications systems including five successful launches of UK and NATO satellites using facilities in Florida for Titan and Delta launches and in French Guyana for Ariane (the picture on the right is courtesy of CSG Kourou).
In 1994 I moved to a new position as Director of Communications and Information Systems Engineering with responsibility for overcoming the problems which the Ministry of Defence was then having in the effective acquisition of large computer based systems involving extensive amounts of software.
This work was not easy, primarily because it proved impossible to convince others within MOD of the substantial changes in attitude and approach which would be needed to successfully implement such systems.
Interoperability in NATO

 Since
the mid-1980s I was active within NATO in pressing forward with technical
efforts to improve the effectiveness of defence computer based systems.
This work involved efforts to persuade NATO countries to adopt common standards
within their respective computer based command and control systems; it also
involved efforts to move towards the more extensive use of commercial products
and standards.
Since
the mid-1980s I was active within NATO in pressing forward with technical
efforts to improve the effectiveness of defence computer based systems.
This work involved efforts to persuade NATO countries to adopt common standards
within their respective computer based command and control systems; it also
involved efforts to move towards the more extensive use of commercial products
and standards.
I spent the last eighteen months of my defence career as the Deputy Director of the SHAPE Technical Centre in The Hague. This appointment was cut short by a reorganisation in which the Centre was incorporated into the NATO C3 Agency in July 1996.
Information Security and Cryptography
By the mid 1980s it was clear that the cost effectiveness of defence computer based information systems would increasingly depend on the exploitation of products intended primarily for the civil market. It was also evident that inappropriate MOD acquisition practices and ineffective GCHQ policies on information security were having a disastrous impact on the cost, the affordability and the performance of such systems.
In the 1970s powerful new cryptographic techniques had been discovered (we now know that they had been previously discovered and kept secret by GCHQ) but they required large amounts of computer power for their implementation. By the late 1980s, however, high performance, low cost computer systems made these methods both practical and highly attractive. Cryptography implemented in software had arrived together with new algorithms that were especially well suited for use within network based information systems where they offered the potential to achieve affordable information security both within defence and more widely.
There were thus good prospects for major improvements
in systems performance, and for reductions in cost, provided only that these
new approaches could be rapidly introduced into the commercial products
and systems from which future defence information systems would be built.
At the same time the growing commercial interest in the security of network
based information systems provided an environment which would promote the
convergence of defence and civil interests in this field.
 As
a result of these developments I initiated a Security in Open Systems Technology
Demonstration Programme with the objective of promoting the convergence
of defence and commercial interests in the exploitation of cryptographic
security solutions suitable for use in open systems environments such as
the Internet.
As
a result of these developments I initiated a Security in Open Systems Technology
Demonstration Programme with the objective of promoting the convergence
of defence and commercial interests in the exploitation of cryptographic
security solutions suitable for use in open systems environments such as
the Internet.
I also co-operated with Steve Walker in the United States in the development of the International Cryptography Experiment, an informal alliance of groups across government and industry interested in finding an acceptable way of implementing internationally interoperable cryptographic security solutions.
My Differences with GCHQ
Prior to 1996 the Government Communications Headquarters (GCHQ) was opposed to much of my work in the information security field because this was intended to encourage the spread of cryptographic information protection outside of government. This is a theme I pursued while working in MOD in order to achieve affordable defence information systems and it is one I have continued to pursue since leaving MOD because of the need to protect the information (and the information systems) on which all of society now increasingly depends.
GCHQ have opposed such developments in the past because of the impact that they might have on their ability to collect electronic intelligence. They maintained this stance well into the 1990's, with no evidence of any serious concern for its detrimental impact on other government departments or for its impact on UK taxpayers. Historically they have also opposed any effective scrutiny of this policy other than in committees where the representation has been carefully arranged to ensure that the policy would never be seriously challenged.
From 1988 until 1996, while working in MOD, I pressed for this policy to be changed. Moreover, since the early 1990s I also sought changes in the related US government policy because of the importance of US based companies in global IT markets and the resulting need for them to be able to offer the secure products on which cyberspace safety and security and electronic commerce increasingly depend.
While I was in MOD in the early 1990's GCHQ made several attempts to undermine my position as a Director for secure systems acquisition. In the US the authorities were more constructive and were prepared to discuss my concerns. My thanks go to them for this.
In pursuing these efforts I have been pleased to find that many people within government were (and are) concerned about the impact of outdated GCHQ policies on their departments and on UK taxpayers. Within MOD I was pleased to have the support of a number of senior colleagues who shared my unease about the undemocratic and unethical way in which these policies were being sustained by preventing effective debate, even within government, about their true value and their full consequences.